DDoS Extortion – Prepare Yourself
By: Darin Barton CISSP, CISA
2016 has seen an increase in DDoS extortions for two simple reasons – it’s low risk and companies are willing to pay. The question is, what would you do?
In March 2016 a group calling themselves the Armada Collective began sending emails to a variety of businesses providing on-line services. These email indicated that they would soon be facing a DDoS (Distributed Denial of Service) attack in the 1TB range for an extended period of time unless they ponied up 20 Bitcoin  (approximately $4,500.00 USD ).
(approximately $4,500.00 USD ).
It turns out this particular “group” was a mimic of the original Armada Collective, a credible group of cyber-criminals active since 2014. The original Armada Collective were suspected members of Bitcoin extortion group DD4BC (Distributed Denial for Bitcoin) who were arrested in January of 2016. Their extortion emails were slightly different from the mimic-Collective in that they would consistently identify a specific time and date to conduct a sample DDoS attack to prove they were serious. The test attacks would consistently generate 5-10Gbps of traffic and companies would often pay.
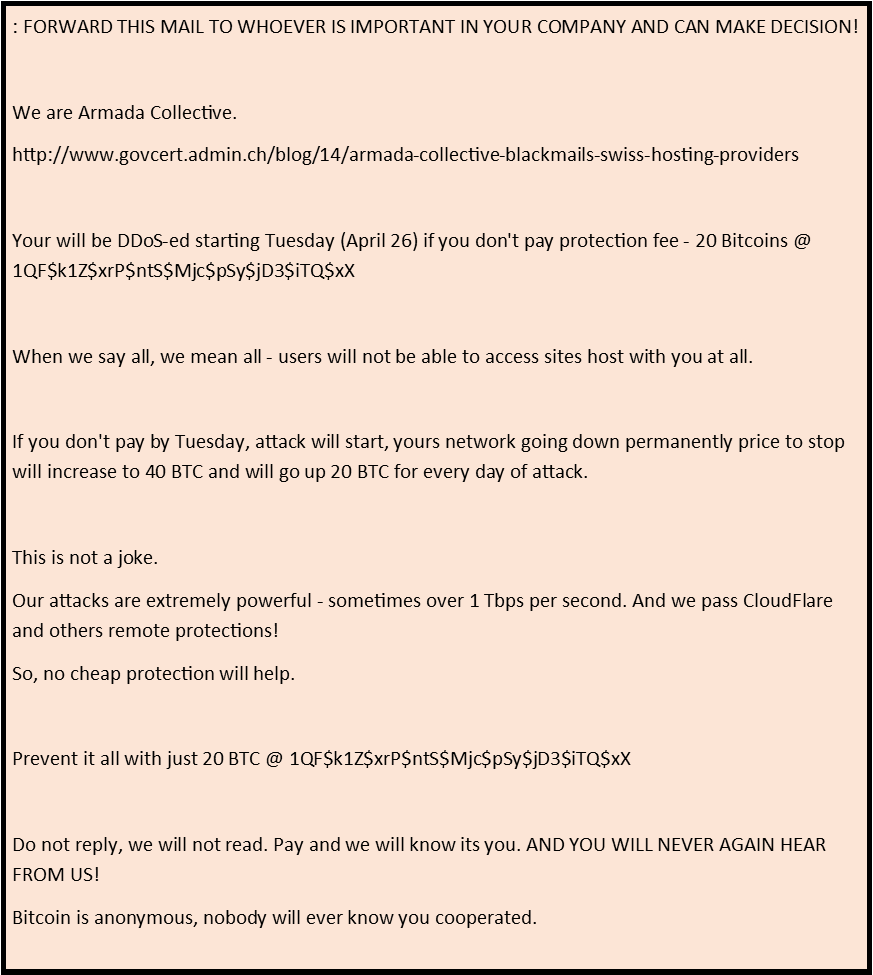
Here is a copy of a recent extortion email from the mimic Armada Collective:
These extortion attempts generate a great deal of concern and angst within companies receiving them. Having never faced these threats before, with a little bit a research, they can quickly ascertain that the threat might be credible. When your company (and customers) depend on the Internet and you’re faced with a 1Tbps DDoS attack, paying the extortionists demands requires some consideration.
A few things to consider
- Payment does not mean you wont be attacked or ransomed again.
- While some mimic groups can execute a DDoS attacks, most of them do not follow through.
- 1Tbps DDoS-While Possible is Not Probable: According to Arbor Networks, specialist in DDoS mitigation, the majority of DDoS attacks never exceed 35Gbps which can be mitigated in several ways.
The final thought
If you receive one of these extortion email – DO NOT PAY! In most likelihood, you will not be attacked and paying does not guarantee that you won’t be ransomed again. More importantly, if everyone would stop paying ransoms then this type of cyber-criminal activity would cease to exist.
Notify the RCMP and/or FBI and take immediate mitigation steps to ensure you are protected.
Determine if the cost of mitigation is worth it – paying more for mitigation than will be lost in business or brand equity is worth knowing. And, sometimes paying a ransom doesn’t benefit your brand equity as identified in this article by GovTech.
There are plenty of DDoS mitigation techniques available and a wide variety of solution partners and manufactures to choose from. My recommendation: check out Imperva/Incapsula and Arbor Networks for DDoS protection for your web sites, network and infrastructure.
Having a hardware DDoS appliance at your networks point-of-presence or a WAF appliance capable of DDoS protection is always a good idea but leveraging the cloud for web site and infrastructure DDoS protection is your best bet for immediate coverage and more important for sustained attacks over 40Gbps. In addition, your upstream ISP may have solid DDoS protections in place. Work with them on monitoring and detection and next step mitigation.
:Darin Barton CISSP, CISA is a senior security professional in Toronto Canada, with 20+ years experience in cybersecurity and investigations and currently employed with Access 2 Networks Inc. (A2N).